Security-By-Design ProvenRun.
It’s all about it, nothing else!
The IoT and cybersecurity landscape
The Internet of Things (IoT) is the intersection of the physical and digital worlds. The proliferation of connected devices and increasingly complex use cases (such as autonomous systems and transportation) create new experiences and opportunities. But it also creates the risk of vulnerabilities that could have catastrophic consequences, given the IoT’s control over physical operations. This requires a foundation in digital trust, functional convergence of the IoT and cybersecurity, and an early-stage integration of cybersecurity in the architecture design. For example, in automotive, it means cybersecurity should be built in at the component level and rigorously tested from initial boot to system interaction.
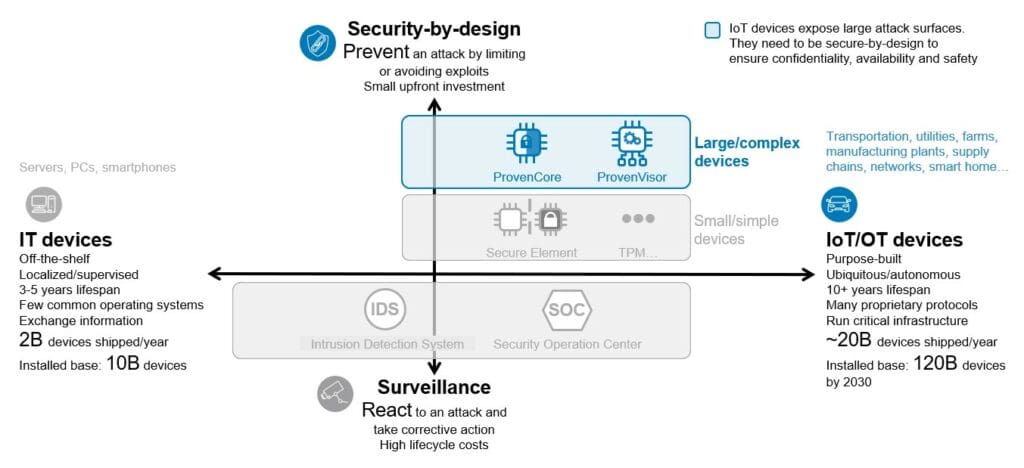
How to secure-by-design
As a pre-requisite to defining security-by-design requirements, a Security Assessment has to be performed in order to define what needs to be done for the product’s security. The product should then be designed and pre-configured with functionalities that are based on well-established security practices and that are reduced to the strict minimum required for system operations. Another important aspect, is that security need to be integrated at every stage of the product’s development, covering the entire product life-cycle (Security-life-cycle) starting from its design and ending with its disposal, as opposed to adjusting or adding security features afterwards.
The anatomy of remote attacks
In the case of the Internet of Things (IoT) and Cyber Physical Systems (CPS) where (massive) remote attacks are the most critical ones, the security-by-design requirements will be guided by the different phases of attacks:
#1 The identification phase
When addressing the identification phase of the attack, security architects and developers will have to consider potentially sophisticated physical attacks. Technologies and know-how to resist to such attacks are widely available and, in the end, the only issue is cost. So, the main strategy will be to keep to the very minimum the number of assets that need to be protected against sophisticated and expensive hardware attacks, and/or to minimize their value for attackers. Secure elements, HSMs and cryptographic processors can be used for that purpose, provided that the list of assets has been brought down to a few (root) secrets and keys that only need to be stored, and used to perform cryptographic operations. Even more important is to build a security architecture that reduces the value of assets by ensuring in particular that if such assets are compromised during the identification phase on one device, they cannot become key in performing the exploitation attack on a large number of remote devices. Once the problem of resistance with respect to the identification phase has been properly handled, physical attacks don’t have to be considered anymore, besides side-channel attacks that can be addressed by using state-of-the-art know-how and technologies.
#2 The exploitation phase
When addressing the exploitation phase of the attack, protection against logical attacks becomes the main challenge, and this is quite new. Resisting to logical attacks indeed has been until recently the easy and marginal part of the security challenge. This is because the hardware components to secure were both very small and had very small attack surfaces. But this situation is radically changing, mainly due to the much larger attack surface exposed by IoT and CPS products and situations where assets that need to be protected are not just virtual, but also physical: goods, infrastructures, lives, etc. In effect, an analysis of the attacks reported in conferences and in the press shows the ever-increasing importance of logical attacks. Hackers typically exploit errors (in the large sense) to break into systems: low-level implementation bugs, protocol or specification flaws, design, configuration or initialization errors, violations of organizational security policy, etc.

